I just did a self-assembly of JTAGulator. This simple and amazing device indeed works and shortens JTAG pinout search from days to seconds. AMAZING! I have some spare devices to sale cheap in EU, if you want one let me know! :-)
JTAGulator is an open source hardware tool, created by Joe Grand / Grand Idea Studio, that assists in identifying OCD connections from test points, vias, or component pads on a target device. All you need is a target device, bunch of tap wires / cables, USB-Mini cable, and serial terminal to operate JTAGulator.
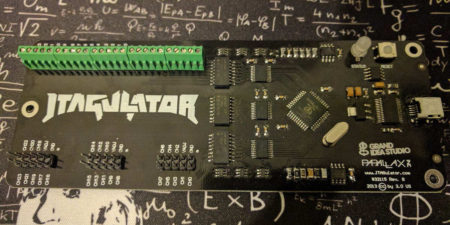
On-chip debug (OCD) interfaces can provide chip-level control of a target device and are a primary vector used by engineers, researchers, and hackers to extract program code or data, modify memory contents, or affect device operation on-the-fly. Depending on the complexity of the target device, manually locating available OCD connections can be a difficult and time consuming task, sometimes requiring physical destruction or modification of the device.










